Initially, I was reluctant to try a YubiKey because it's configured such that GPG/PGP private keys can only be written to it and cannot be exported. Additionally, my AIR doesn't have a USB-A port, and the four YubiKeys I bought on discount two years ago all use USB-A, so I found it too troublesome to use.
Later, after some casual research, I learned that I could generate several subkeys through GPG Suite, back up the private keys first, and then export them to the YubiKey. This way, I wouldn't have to worry about losing the private keys. So, during my free time this week, I began my imperfect practice with Yubico's GPG/PGP.

Before I proceed with the text, I need to mention a pitfall I encountered. Although the YubiKey 5 supports DSA public keys, it does not support DSA private keys. Initially, I chose a DSA signing key to keep the signature size smaller, but I couldn't import it into the YubiKey, which forced me to generate a new RSA subkey for signing and subsequently update the private keys on GitHub and key.jdzhao.com. For those starting fresh, you might want to avoid this issue.
The complete process is well-documented online; here, my purpose is twofold: to keep a record and to share key points with the audience.
1.YubiKey’s PIN and PUK
It's important to note that the PIN used for GPG and the PIN/PUK used in the YubiKey Manager software for PIV are different concepts; they are independent of each other and should not be confused.
When preparing to use the YubiKey for GPG, we need to modify the USERPIN (used for daily signing and encryption), ADMINPIN (used for importing private keys), and PUK (used for resetting the PIN after it's locked) through command-line tools.
In command-line mode, we enter the YubiKey operation interface by using gpg –edit-key, and here is a screenshot of the help section.
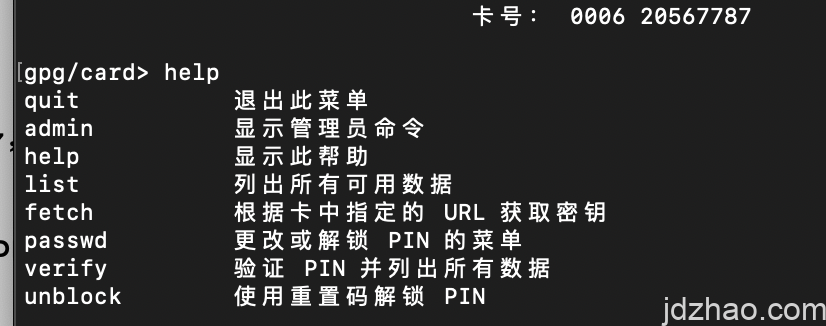
By entering "admin", you can access the admin interface, where you'll see the following operational commands.
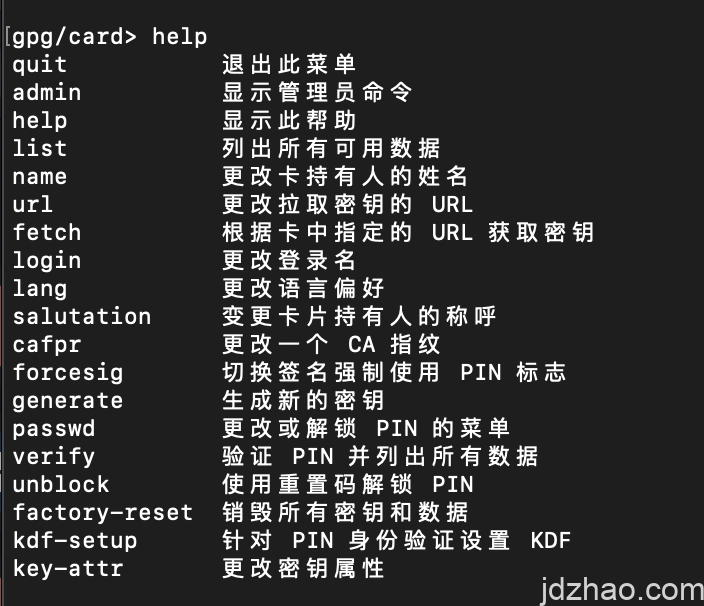
建议输入passwd,修改PIN、ADMIN PIN,以便私钥的修改和签名的安全。
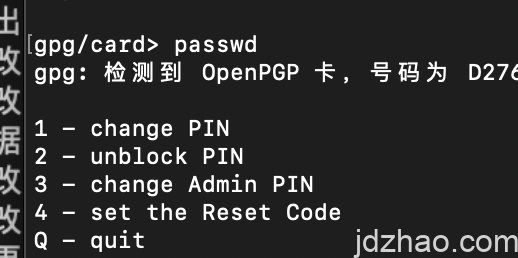
2.. About Generating GPG/PGP Keys
To allow for backups, we opt to generate private keys using third-party software and then import them. On macOS, you can use GPG Suite, and on Windows, it's recommended to use GPG4Win. Start by generating a primary key, and then it's advisable to create three subkeys for signing (S), encryption (E), and authentication (A). Managing subkeys later—such as adding, revoking, or deleting—can affect our public key, leading to the hassle of redistributing it multiple times.
3. Backing Up Private Keys
After generating them, first back up your public keys, subkeys, and revocation certificates. For GUI, you can directly use the software for backup. If using the command line, you can back up like this:
gpg –armor –export-secret-keys your-key-id > privkey.asc
After exporting, it's recommended to package or compress and encrypt the data for storage in a secure location.
4. Importing to YubiKey
Operations for importing to YubiKey must use the command line tool, and typically, only the subkeys are imported, not the primary key.
enter the following to see the overall situation of the key: gpg –expert –edit-key USERID (usually an email or fingerprint) This procedure helps manage the keys effectively and ensure their security when using with YubiKey.
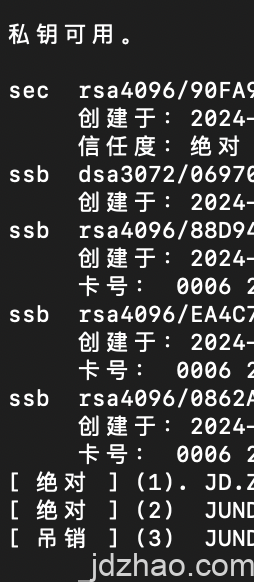
In the GPG key management interface, sec denotes your primary key, and ssb refers to your subkeys. Generally, you cannot select multiple keys at once; you need to import them one by one.
y default, the first key is labeled as Key 0. You should skip the primary key and enter key 1 to select the first subkey by default. Once selected, an asterisk (*) will appear next to it, indicating that it has been selected.
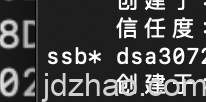
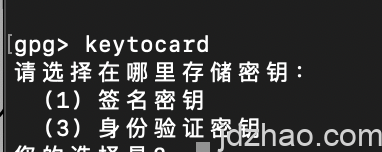
Next, type keytocard, which will prompt you to choose a slot. Typically, these slots correspond to the different functions of the subkeys:Signing (S slot) Authentication (A slot) Encryption (E slot) Each slot on the YubiKey is designed to hold a specific type of subkey, ensuring that each function—signing, authentication, and encryption—is properly isolated and managed. This setup enhances the security and functionality of the keys stored on the device.
5. YUBIKEY Status
You can check the status of your YubiKey by using the following command:gpg --edit-card.This command will provide you with an interface that displays various information about your YubiKey, such as the card version, serial number, and the user data stored on the card. It also allows you to perform other card management functions directly from the command line.
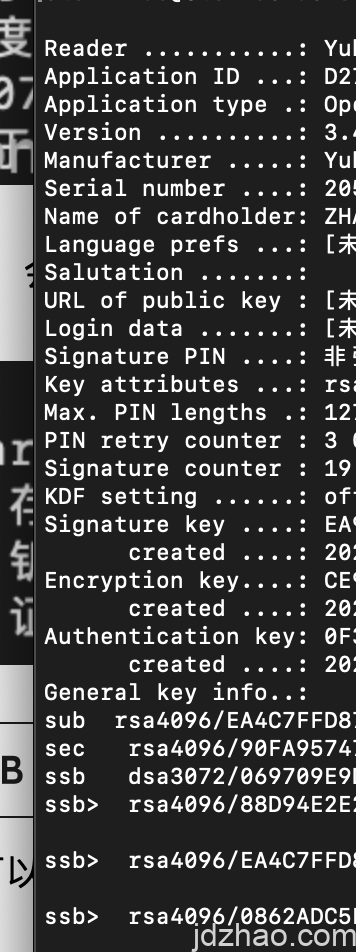
You can view the overall condition of your YubiKey, such as the settings for PIV (typically used for system logins), and the various subkeys that have been imported. The subkey used for AUTH is primarily for logging into and accessing remote servers, which is a topic I plan to discuss in detail in a separate article when time permits.
六、日常使用
请注意,导入私钥的时候,会输入你的私钥密码、ADMIN PIN(请注意是ADMIN PIN)
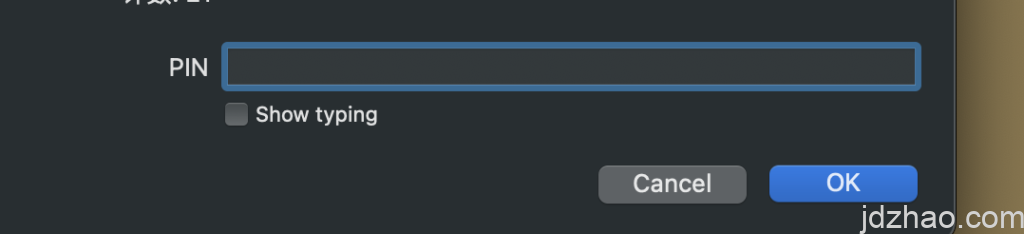
日常使用,是输入USER PIN(普通的PIN),下图是日常加密、签名的PIN窗口(如果你设置了必须接触YUBIKEY ,那么输入PIN后,还需要接触YUBIKEY才能完成,YUBIKEY处于等待模式时,KEY上的指示灯会常闪)
These are the key points concerning the use of YubiKey for GPG/PGP applications. If I think of anything else, I'll add it later. I welcome further discussion and exchange of ideas on this topic.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA256
本处签名,通过YUBIKEY的RSA子钥签发
你可以通过key.jdzhao.com下载我的公钥
并验证本签名的有效性。
-----BEGIN PGP SIGNATURE-----
iQIzBAEBCAAdFiEE6pG3rRqQ57EQTPmw6kx//Ye6jBYFAmY6RIgACgkQ6kx//Ye6
jBZdFQ//ckGWmCOk82r3dQa8GN3Bg8BLiuzX1i7rHs1fdqreBZwRJ5JcXtPOQ2aK
JY1VTpK6P7rJA0j3E5fa3fJ/fQ9+NSLIxD4UHJukIMQMqhN6FbAwf3EUXFS5QRg0
urJ1z4ZkfqpSpMCVABj6cs5P6XaXWa6IU7U3qzv278pN46JuvbWPynFYO+MmbZHK
MM2c4z+hi88MMWa6tSp31gclB7DwmEN2ekP8TggQKck5moO+C2F1KDy+L/31Y+LO
SxOq5EuWk9MObLWzzd8lz5MbBTJswfPc/+wIwNwtHVmi0Qxi80UabXb1dIpGqliZ
bo5e5RQgiULYNv8Kf582suXV8nnTZkRwknB9N/jOp4HecbMInkMGoNj418b1JXS+
Ut+/PT/DXQMrUrrt1OEACe5+ocbHFs9Y6pjXF7QhaANX8Cfrpf+XjnCA28PmXJT3
4mtegbTzyVybcB+6kBKpjd8f56dFoiEZ4qGsSM1k7y25KbL944TijXUDwBLrc3Cx
B3BcfDWvJVYg78nw57zzrmZtRk4lNQsg+Mr+OrhOjhRWWPzxnLVq7yioKOwN4Z/1
MVi0MlxfnDCJ2FXxmaU3aD4dMLQhYRoqkNt7i4ajLeAJ7LIraELkEajpOE/VooWv
So9xR+UbLqCa4w7lMaTUmKlRzegjyZsSbE3CI2uTeilfvZYa9pI=
=FmbH
-----END PGP SIGNATURE-----
GoodBoyboy
MR.Zhao