《GPG/PGP Tinkering Diary: Proving I Am I》, we discussed the methods of using GPG/OPENPGP for signing and encryption.
However, a question arises regarding the validity of the timestamp when it comes to signing important documents, publishing public keys, etc. Although GPG signatures contain a timestamp, this timestamp is derived from the system time and can be falsified. Let's assume two scenarios: you want to declare copyright ownership or the signing time of a public key. How can you effectively prove that you were the first to publish? Coincidentally, we can combine GPG/OPENPGP with Opentimestamps to enhance this self-proof.
PGP signatures provide proof of identity and document integrity, but their timestamps rely on the signer's system clock, which may be questioned. OpenTimestamps offers independent, tamper-proof time proof, which can enhance the credibility and legal effectiveness of the overall evidence. By combining PGP signatures with OpenTimestamps, stronger legal proof of a document's existence, integrity, and time can be provided.
Let's use the example of timestamping a public key file. We have already obtained an ASC public key file and a SIG signature file for the public key. Now we will timestamp them.
First, you need to install OpenTimestamps. See the details at:https://github.com/opentimestamps/opentimestamps-client/blob/master/README.md
I chose the Python method. After installation, we switch to the folder containing the public key and signature files and execute:
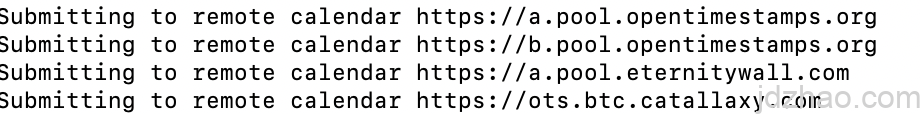
ots stamp *.asc.sig
ots stamp *.asc
At this point, two OTS files will be generated in the folder, which are the timestamp proofs for the corresponding files. You can also see the submission status.
Viewing Hash Values and Verification Status
The timestamp records for the files are made using hash values. We can view the hash values with the following command:
shasum -a 256 *.asc.sig
We can also use the ots verify command to check the proof status. Since the upload needs to be confirmed by the blockchain, you might see that the verification is pending. The commands are:
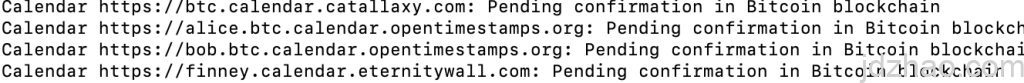
andhttps://opentimestamps.orgTo verify the timestamp, you can upload the OTS files along with the original files to https://opentimestamps.org. However, for security reasons, it is recommended not to use the website for queries. Instead, you can use the command-line tools provided by OpenTimestamps.

By hashing and timestamping both the original file and the signature file separately, you can ensure the existence and integrity of the original file and the signature file.
Publish Your Signature and Timestamps
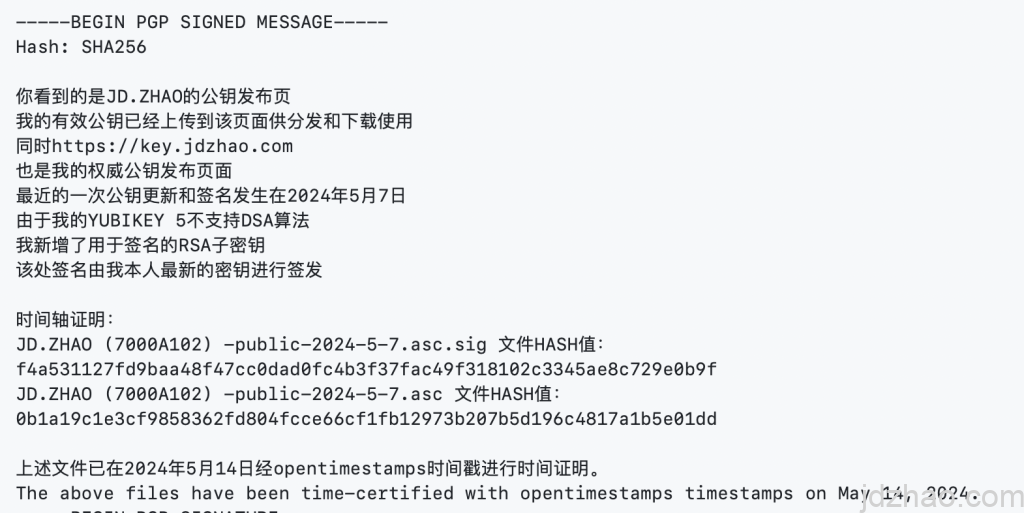
Summary: This is just an exploration and a method to experiment with. In practice, it may not be necessary to go through such a complicated process. However, it is indeed an effective proof method. This approach not only proves your identity but also proves that you were the earliest publisher. Even if someone later claims to have authored the file or if the file is misappropriated, you can effectively prove your rights.


Leave a Reply