Remember in the previous article 《YUBIKEY的GPG/PGP使用不完全实》 "Incomplete Practice of Using YUBIKEY's GPG/PGP," we also generated a subkey for AUTH.
One use of this subkey is to authenticate via SSH using the GPG-AGENT on the server, without having to generate a separate set of SSH keys, which helps in unified management.
Today, we'll practice this on a Mac system. First, insert your YUBIKEY (if you don't have one, GPG software alone will suffice).
Enter gpg --list-keys --keyid-format LONG to find the ID of the subkey used for AUTH.
It should look something like this: sub rsa4096/0*******************5E 2024-05-07 [A] [expires: 2029-05-06]
Open ~/.gnupg/gpg-agent.conf with any text editor and add enable-ssh-support to enable SSH support in gpg-agent.gpg-agent中启用SSH支持。
Add the subkey ID~/.gnupg/sshcontrol Add the ID 0*******************5E to ~/.gnupg/sshcontrol.
Tell the terminal to use the gpg-agent socket instead of the ssh-agent:
export GPG_TTY=$(tty)
export SSH_AUTH_SOCK=$(gpgconf –list-dirs agent-ssh-socket)
gpgconf –launch gpg-agent
Verify the setup by executing ssh-add -l. You should see the subkey added. If not, try restarting the terminal.
4096 SHA256:U****ifS/j********H5k cardno:20 567 787 (RSA) 【这说明是yubikey】
4096 SHA256:Uq***QWifS/j********H5k (none) (RSA)【这说明是本地的key】
Export the public key. Remember, this is not your GPG public key:
gpg –export-ssh-key i@jdzhao.com
Add the exported public key to the ~/.ssh/authorized_keys file on the remote server.
You're all set! If you encounter any issues, use ssh -vvv root@1.1.1.1 -p 22 to troubleshoot.
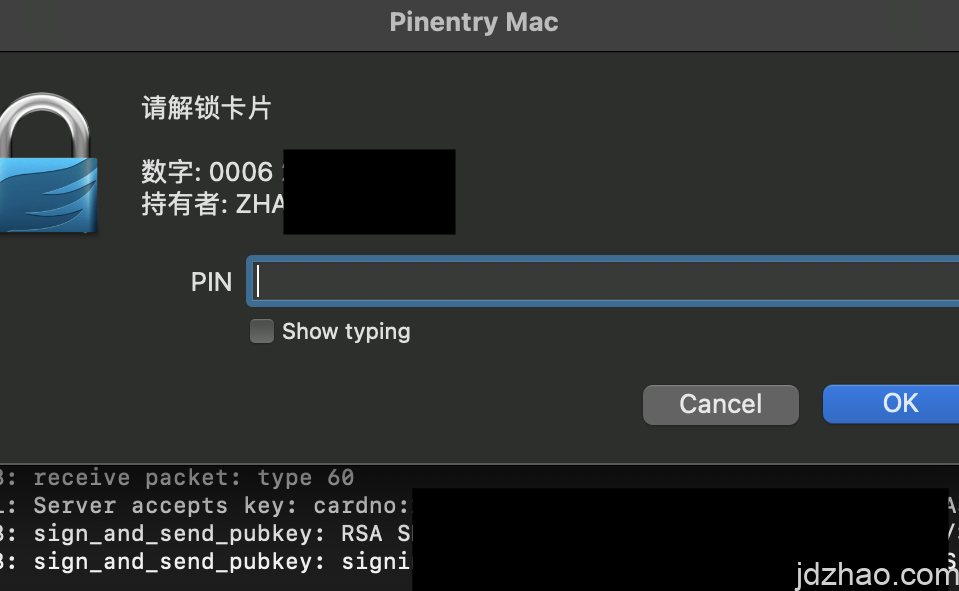
Summary: Using GPG allows for unified key management, avoiding the need for an additional set of SSH keys. The reason for not choosing the more convenient FIDO2 is that FIDO2 keys are bound to the hardware key itself. If the key is lost, there's no way to recover it, leading to potential significant issues.

Leave a Reply