Although I had heard of PGP before, I had never actually used it until recently when I delved a bit deeper into it. I've made some notes to share with those who might be interested.
GPG and PGP have some differences. Both GPG (GNU Privacy Guard) and PGP (Pretty Good Privacy) are encryption technologies used for data encryption and digital signatures to ensure information security and identity verification. The main difference is that GPG is a free and open-source alternative to PGP, following the OpenPGP standard, while PGP was originally proprietary and is now maintained by Symantec.
Main Uses:
Signing texts or files to ensure the sender's identity is genuine and prevent tampering.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA256
给这段话签名,是为了证明该文本是由JDZHAO在5月4日发布的。
-----BEGIN PGP SIGNATURE-----
iHUEAREIAB0WIQTLEr80LL/GAfzwNHsGlwnp1It2awUCZjUMzwAKCRAGlwnp1It2
a6QeAQCJ1sLAeb8XjvGU18cGHiRY8MqdHytJQrACw4uyA4ex/AD+IKgQmHqTdNaG
vOq5eGk3UPSqxKyqCAfPexXGm7xIKL8=
=TGfV
-----END PGP SIGNATURE-----
At this point, if you have saved my public key, you can right-click to select all of this text, choose "Verify signature," and a "trusted signature" message will pop up. The process is the same for file operations.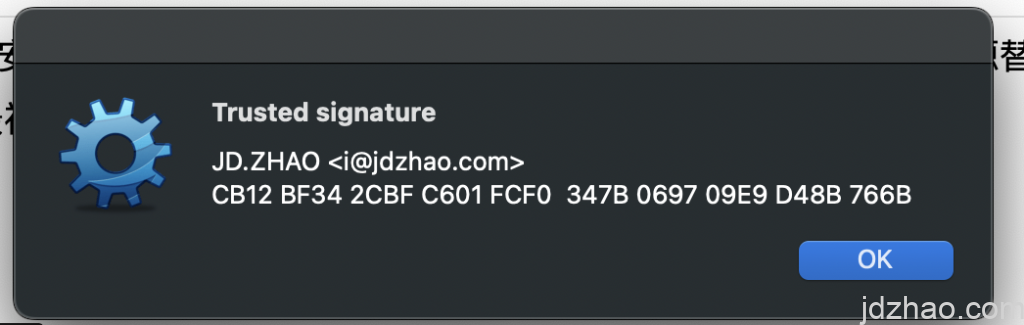
encrypt or decrypt
As shown, if you need to encrypt text, simply enter the text you want to encrypt into any text editor, and then select "encrypt selection."
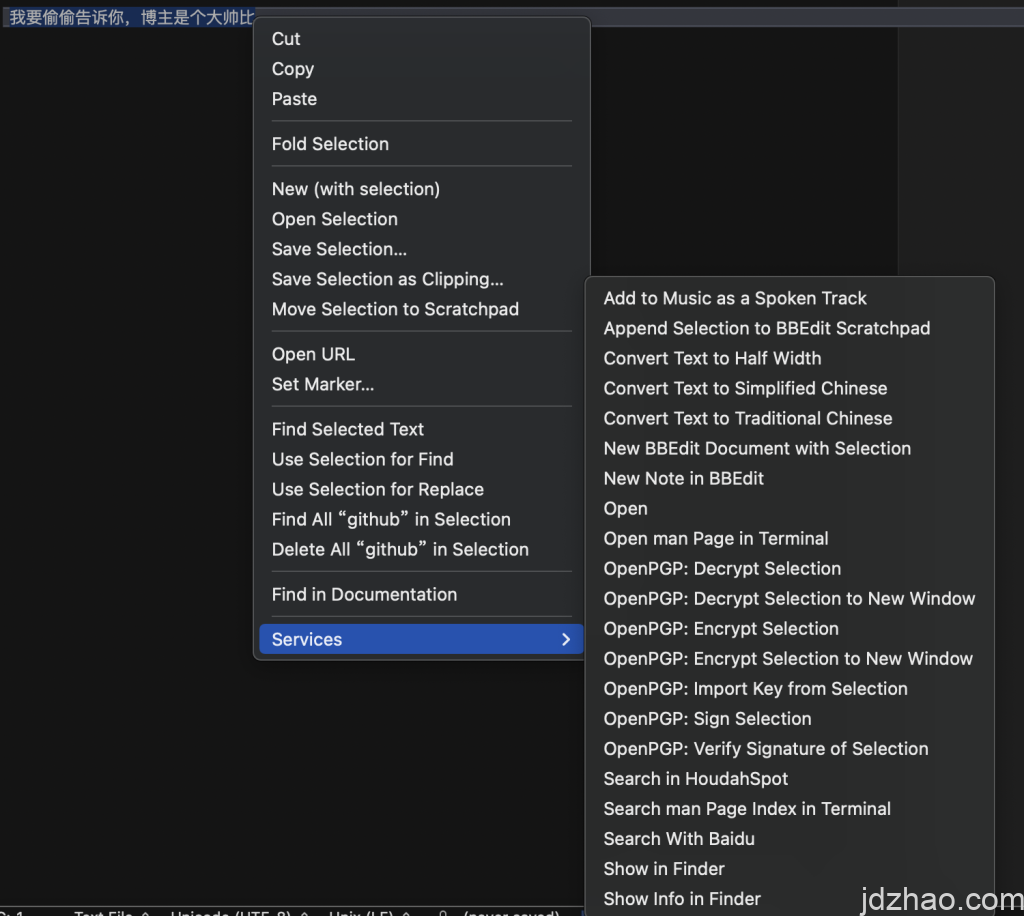
It's important to note that your signature must have a "recipient." For example, if you download the blogger's public key, then select the blogger as the recipient and encrypt using your private key, the blogger can then decrypt the message using their private key and see it. Therefore, this process can't be demonstrated here. If anyone wants to try it, you can download the blogger's GPG public key, encrypt a message for the blogger, and post the encrypted text in the comments section. The blogger will then be able to reply to you with the decrypted information.
II. What software to use
The blogger uses GPG Suite, which can be downloaded from https://gpgtools.org. Please try others on your own. https://gpgtools.org 即可。其他的请大家自己尝试。
III. Points to note
There are several important points to be aware of, as mistakes can cause significant issues.
When creating a private key with GPG Suite, it automatically generates a subkey for encryption and decryption. Therefore, be careful not to accidentally delete your subkey if it's in use, as this will prevent you from accessing previous information.
It is recommended to create two subkeys: one subkey for signing, using DSA encryption, which is more suitable for web publication due to the friendly length of the signature; and another subkey for encryption and decryption. The reasons are as follows:
Choosing between RSA and DSA depends on your specific needs and environment. Here are some considerations:
- 密钥长度和性能Key Length and Performance: RSA key lengths are generally longer than DSA keys, which may lead to higher computational resource consumption during encryption and decryption. If you need higher performance for encryption operations, consider using DSA. However, note that key length is directly related to security; the longer the key, the more difficult it is to crack.
- 支持性Support: RSA is more widely supported as an encryption algorithm, with many encryption libraries and software providing support for RSA. Support for DSA is relatively less. If you need to interact with different systems or software, RSA might be a better choice.
- 安全性Security: Both RSA and DSA are widely accepted as secure algorithms, but there might be some differences in specific situations. Generally, RSA might be more susceptible to certain attacks when the key lengths are equal, so consider your security environment and security requirements when choosing an algorithm.
- 签名性能Signature Performance: DSA is typically faster at generating and verifying signatures than RSA. If your application requires frequent signing operations, DSA might be more preferable.
If you are more concerned with performance and shorter key lengths, DSA might be more suitable. However, if you need broader support, higher security, or more flexibility in key length, RSA might be the better choice.
Public keys need to be published so that those who wish to communicate with you can download and use them.https://keys.openpgp.org Therefore, it is best to configure your GPG private key before exporting and publishing your public key. GPG Suite also offers a publication service at https://keys.openpgp.org, where the main ID is an email address, and publication only proceeds after email verification, which is reliable, though I have not used it. You might consider publishing your public key on your own website or GitHub for convenience. https://key.jdzhao.com 和https://github.com/zhaojundong/me 。
There are also options like Yubico for importing hardware keys. I tried Yubico 5, but found it inconvenient, and the two I bought were not USB Type-C, which is not compatible with newer laptops that lack a Type-A port. So, I decided not to complicate things further.
If you want to use it for signing on GITHUB, the email associated with your public key needs to match your GitHub email. GPG can add multiple USER IDs (i.e., multiple emails), and GitHub also requires verification for multiple emails, so avoid adding too many.
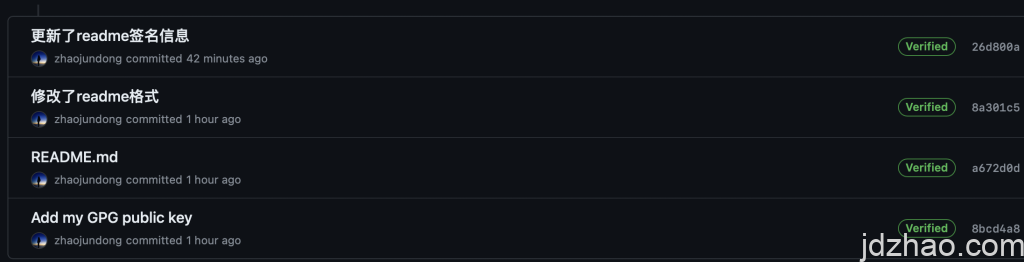
Signing or encrypting messages has strict format requirements. If you are publishing on a web page, please pay attention to the layout. For example, I use "code" mode or the
tag.

Leave a Reply